Note for Buildup and Teardown
Please bear with us during buildup and teardown. The GPN 2023 build up takes place on Wednesday, June, 7th and tear down starts on Sunday, May, 11th.
Please understand that we're quite a busy folk during that time and we have a lot of stuff getting set up or torn down. This means, we're not angry with anybody, but have a tight schedule we have to follow in order get everything done in time - especially during build up on Wednesday.
If we're very busy or too exhausted and don't find the time to answer your questions or requests, please give us some time and come back later when there is less business at the GPN NOC Desk.
Network
Yes, we've got internet. Some networks are unfiltered, e.g. no firewall, no NAT and use public IP adresses. Please make sure, all your devices are up-to-date and services running on your devices are configured securely. We recommend to activate a firewall. There are firewalled networks as well filtering out some of the inbound network requests. For details, see below
Please bring your own network cable (3m - 5m) with you. When connecting your device to the switch, please make sure the cable does not form a tripping hazard or spans between tables.
Wi-Fi (encrypted)
Please consider using a wired connecting in order to save air time. Due to a lot of access points located GPN, HfG and ZKM, air time is really tight.
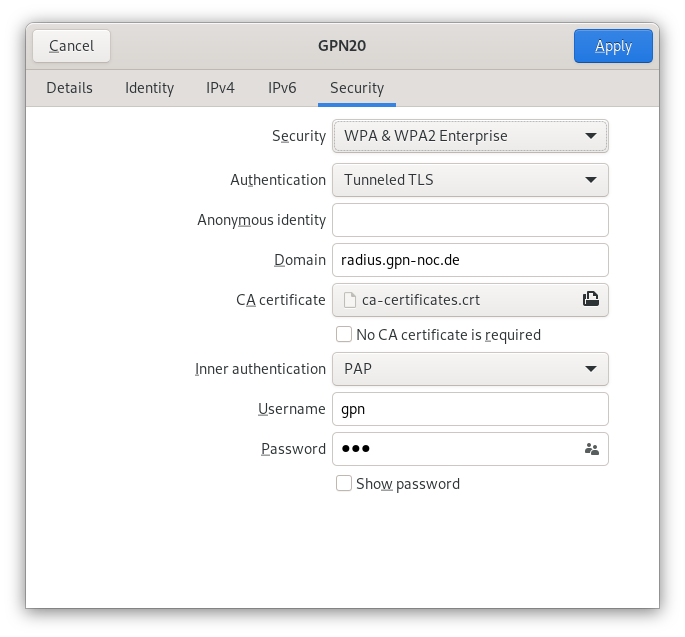
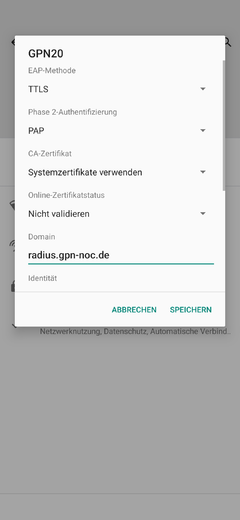
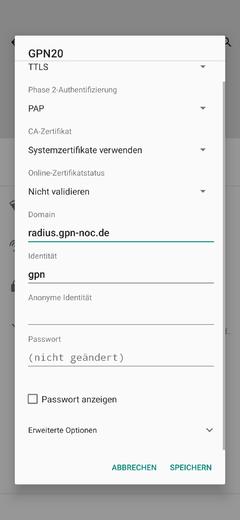
Credentials (Default: Protected from connections outside the event)
- SSID: GPN21
- Mode: WPA2-Enterprise
- TTLS/PAP or PEAP/MSCHAPv2
- (But not TTLS/MASCHAPv2)
- TTLS/PAP or PEAP/MSCHAPv2
- Username and Passwort
- for PEAP/MSCHAPv2:
- Username/Identity:
gpn - Password:
gpn - Domain:
radius.gpn-noc.de - CA certificate:
Use system certificateNote: For Google Pixel 6 (Pro) with Android 12
- Username/Identity:
- for TTLS/PAP
- Domain: radius.gpn-noc.de
- Everything else: <anything you like - we don't care>
- for PEAP/MSCHAPv2:
If you want to check that you really connect to the insecure network of your choice, please verify the certificate of CN radius.gpn-noc.de is issued by Let's Encrypt.
Credentials (Protected from every incoming connection)
- SSID: GPN21
- Mode: WPA2-Enterprise
- TTLS/PAP or PEAP/MSCHAPv2
- (But not TTLS/MASCHAPv2)
- TTLS/PAP or PEAP/MSCHAPv2
- Username and Passwort
- for PEAP/MSCHAPv2:
- Username/Identity:
protect-me - Password:
protect-me - Domain:
radius.gpn-noc.de - CA certificate:
Use system certificateNote: For Google Pixel 6 (Pro) with Android 12
- Username/Identity:
- for TTLS/PAP
- Domain: radius.gpn-noc.de
- Everything else: <anything you like - we don't care>
- for PEAP/MSCHAPv2:
If you want to check that you really connect to the insecure network of your choice, please verify the certificate of CN radius.gpn-noc.de is issued by Let's Encrypt.
Credentials (not firewalled)
- SSID: GPN21
- Mode: WPA2-Enterprise
- TTLS/PAP or PEAP/MSCHAPv2
- (But not TTLS/MASCHAPv2)
- TTLS/PAP or PEAP/MSCHAPv2
- Username and Passwort
- for PEAP/MSCHAPv2:
- Username/Identity:
no-firewall - Password:
no-firewall - Domain:
radius.gpn-noc.de - CA certificate:
Use system certificateNote: For Google Pixel 6 (Pro) with Android 12
- Username/Identity:
- for TTLS/PAP
- Domain: radius.gpn-noc.de
- Everything else: <anything you like - we don't care>
- for PEAP/MSCHAPv2:
If you want to check that you really connect to the insecure network of your choice, please verify the certificate of CN radius.gpn-noc.de is issued by Let's Encrypt.
wpa_supplicant.conf
network={
ssid="GPN21"
key_mgmt=WPA-EAP
eap=TTLS
identity="wiki"
password="binzufauldaspwzuaendern"
# ca path on debian 11.x, modify accordingly
ca_cert="/etc/ssl/certs/ISRG_Root_X1.pem"
altsubject_match="DNS:radius.gpn-noc.de"
phase2="auth=PAP"
}
netctl
Description='GPN21 secure WPA2 802.1X config'
Interface=wlp4s0
Connection=wireless
Security=wpa-configsection
IP=dhcp
ESSID=GPN21
WPAConfigSection=(
'ssid="GPN21"'
'proto=RSN WPA'
'key_mgmt=WPA-EAP'
'eap=TTLS'
'identity="wiki"'
'password="binzufauldaspwzuaendern"'
'ca_cert="/etc/ssl/certs/ISRG_Root_X1.pem"'
'altsubject_match="DNS:radius.gpn-noc.de"'
'phase2="auth=PAP"'
)
Network manager (text file)
Create a file /etc/NetworkManager/system-connections/GPN21.nmconnection with the following:
[connection] id=GPN21 uuid=a60a535f-57cb-4fe8-9688-7ff9bd315311 type=wifi autoconnect=false [wifi] mode=infrastructure ssid=GPN21 [wifi-security] key-mgmt=wpa-eap [802-1x] ca-cert=/etc/ssl/certs/ISRG_Root_X1.pem domain-suffix-match=radius.gpn-noc.de eap=ttls; identity=gpn password=gpn phase2-auth=pap [ipv4] method=auto [ipv6] addr-gen-mode=stable-privacy method=auto [proxy]
Then, start the service:
nmcli c up GPN21
NetworkManager (GUI nm-connection-editor)
Certificate path: /etc/ssl/certs/ISRG_Root_X1.pem
Colocation
YES, we'll have a colocation again and we can provide you with:
- 10GbE SFP+ ports. We do not lend transceivers. We never have and never will - ever!!! The colo switch is a Cisco Nexus and usually accepts a wide range of transceivers.
- 1000Base-T (1GBE) ports / 10GBase-T is available as well.
Please mark your server with
- your nickname.
- and your DECT- or cellphone-number.
- and your e-mail adress to get in contact with you.
Otherwise we have to disconnect your server. We use "Laundry Clip DHCP": get your laundry clip at the NOC Desk and attach it to your network cable. Please bring back the laundry clips after the event.
Please see the local signs for more information.
In case of problems, find us at the NOC desk or call DECT 1209 or 662.
Colocation-Location
The colocation can be found on the 1. OG (2nd floor) on the 'bridge' between both hack centers.
Pixelflut
- You have built your own fancy Pixelflut and want to bring it along to GPN?
- But you don't know where to place it or connect it with enough uplink?
=> Please come to the NOC Desk and ask our staff. We'll be there for you starting Thursday afternoon, e.g. after the Opening (if build up is already finished).
Please also consider limiting the Pixelflut traffic to local traffic, only.
Android 11 Config Screenshots
(Sorry, german language OS)